Monday, September 19, 2005
Andrew Peters at the Coworking Space
Andrew Peters is joining us today in the coworking space, along with Ray Baxter, who officially signed on today. Andrew is a user experience architect, and has worked with such clients as Ask Jeeves and Kodak. Andrew's been to some pretty amazing places, traveling to really interesting parts of the world; it was cool having lunch with him and learning how he hiked deep into Burma, hanging out with the Shan insurgency army there. Wow. Check out his website to learn more about his travels and user experience consulting practice.
Coworking is a way for self-employed writers and programmers to have structure and community. We meet on Mondays and Tuesdays in San Francisco, from 9 AM to 5:45 PM. We are about 5 blocks from Delores Park, in a beautiful converted home run by an art and women's collective named Spiral Muse. Try coworking for free for two weeks. Call me at 510-938-3263 if you have any questions.
Coworking is a way for self-employed writers and programmers to have structure and community. We meet on Mondays and Tuesdays in San Francisco, from 9 AM to 5:45 PM. We are about 5 blocks from Delores Park, in a beautiful converted home run by an art and women's collective named Spiral Muse. Try coworking for free for two weeks. Call me at 510-938-3263 if you have any questions.
Morning Coffee Post: Reverse Engineering
Couple of quick links this morning. Today's theme is reverse engineering.
First, over on Plasser.net the author has done some cool reverse engineering work on meebo.com. Meebo is a new AJAX-powered instant messaging site. The Plasser.net guy has figured out how they continiously query the server in an efficient way; its a good post, and even includes source code on using the technique yourself.
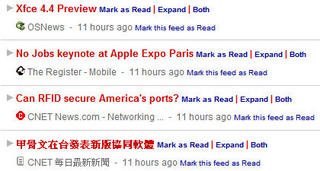
Next, the blogger over at http://blog.yuan.cc reversed engineering part of Rojo, the company I used to work at, and made it's Mark Read functionality more efficient and usable using Greasemonkey. A screenshot of his Greasemonkey script in action (his addition is the new option 'Mark this feed as read'):
Finally, a group of open source hackers has come together to create Red5, an open source implementation of Macromedia's Flash Communication Server (FCS). FCS is an amazing product, making it possible to collaborate with webcams and audio, and to stream shared video, audio, and objects. Unfortunately, FCS is wickedly expensive and completely closed source. FCS works through a proprietary Macromedia protocol named RTMP (Real-Time Messaging Protocol).
These guys are serious; I've been tracking their progress the last week and a half and its been phenomenal. They've cracked a large amount of the RTMP wire protocol; an outside user contributed a Ruby implementation that they created on their own awhile back; and a Red5 programmer has created the beginning scaffoldings of an RTMP implementation.
First, over on Plasser.net the author has done some cool reverse engineering work on meebo.com. Meebo is a new AJAX-powered instant messaging site. The Plasser.net guy has figured out how they continiously query the server in an efficient way; its a good post, and even includes source code on using the technique yourself.
Next, the blogger over at http://blog.yuan.cc reversed engineering part of Rojo, the company I used to work at, and made it's Mark Read functionality more efficient and usable using Greasemonkey. A screenshot of his Greasemonkey script in action (his addition is the new option 'Mark this feed as read'):

Finally, a group of open source hackers has come together to create Red5, an open source implementation of Macromedia's Flash Communication Server (FCS). FCS is an amazing product, making it possible to collaborate with webcams and audio, and to stream shared video, audio, and objects. Unfortunately, FCS is wickedly expensive and completely closed source. FCS works through a proprietary Macromedia protocol named RTMP (Real-Time Messaging Protocol).
These guys are serious; I've been tracking their progress the last week and a half and its been phenomenal. They've cracked a large amount of the RTMP wire protocol; an outside user contributed a Ruby implementation that they created on their own awhile back; and a Red5 programmer has created the beginning scaffoldings of an RTMP implementation.
Subscribe to Posts [Atom]
